The security firm ReversingLabs’ research team has discovered yet another campaign targeting specific versions of the popular crypto wallets Exodus and Atomic.
According to the report, threat actors “have been targeting the cryptocurrency community hard lately.” They’re using various methods to hijack popular and legitimate crypto packages to loot people’s wallets.
However, the researchers highlight that hijacking open-source packages is difficult due to the size of the open-source software (OSS) developer community. The tampered-with OSS packages will be detected.
Therefore, threat actors are working hard to make their methods more obscure. A new technique that ReversingLabs discovered is uploading packages to OSS repositories and having them apply malicious ‘patches’ to local versions of legitimate libraries.
The goal is the same: install an unnoticeable malicious code in a popular, trusted local library.
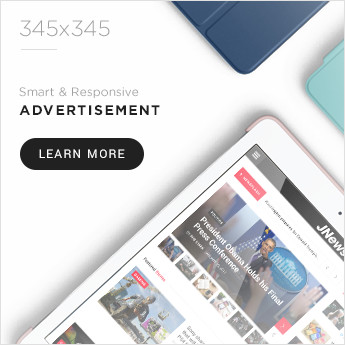
The researchers found “a number of campaigns” in recent weeks attempting this strategy. Notably, on 1 April, a malicious entity published a package, pdf-to-office, to the npm package manager. This package posed as a library for converting PDF to Microsoft Office documents.
Once executed, it would inject malicious code into locally installed Atomic Wallet and Exodus. It would overwrite existing files. “Effectively, a victim who tried to send crypto funds to another wallet would have the intended destination address swapped out for one belonging to the malicious actor,” the report states.
Additionally, this campaign is quite similar to the one the researchers discussed in a research post in March.
In both of these cases, the malicious campaign had no effect on the official Atomic Wallet and Exodus Wallet installers available on the websites.
Aiming for Specific Wallet Versions
ReversingLabs first detected the pdf-to-office package after its update to npm on 1 April. It was removed soon after detection. But a couple of days later, the threat actor published a new version that looked like the first one. They released three versions of the package over a few weeks in March and April with the same functionality.
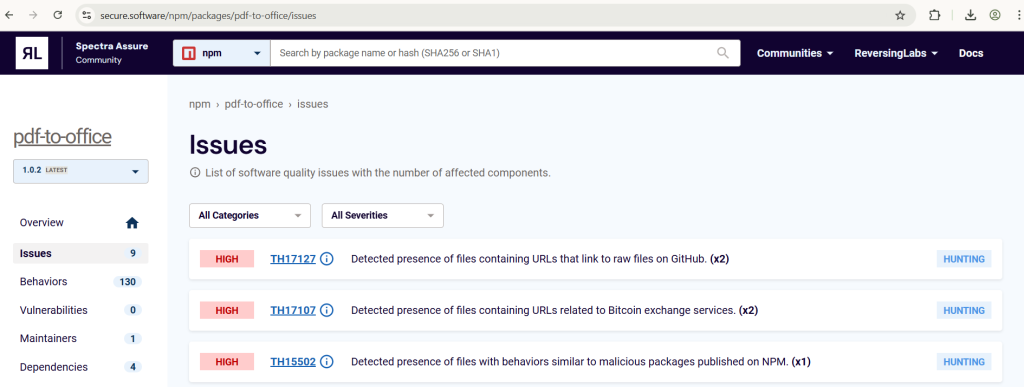
The malicious payload worked to detect the presence of the atomic/resources/app.asar archive inside AppData/Local/Programs directory. Finding it would mean that the unsuspecting user installed Atomic Wallet on their now-infected computer.
Then, the malicious code searched for the archive to overwrite one of its files with a trojanized version that changes the outgoing crypto address. Now, the funds would go straight to the threat actor’s wallet.
“That was the only difference between the legitimate and trojanized file, except that the malicious version of the file was not minified,” the report notes.
Additionally, the threat actors focused on specific versions of Atomic. The attack code would adjust which files were overwritten based on the wallet version it found.
Moreover, there was a malicious payload that attempted to inject a trojanized file inside a legitimate, locally-installed Exodus wallet. It targeted the two latest versions of Exodus.
Also, if the victim removed the package pdf-to-office from the computer, the Web3 wallets’ software would still remain compromised. This means it would continue directing crypto to the attackers’ wallet.
“The only way to completely remove the malicious trojanized files from the Web3 wallets’ software would be to remove them completely from the computer and re-install them,” ReversingLabs concludes.
Meanwhile, North Korea’s Lazarus group has been targeting crypto developers via npm supply chain attacks for months in a highly sophisticated global campaign to steal funds and data.
The post New Malicious Campaign Targets Atomic and Exodus Wallets appeared first on Cryptonews.
Credit: Source link

 RL researchers have identified yet another
RL researchers have identified yet another  https://t.co/lbyNR5cp8Z
https://t.co/lbyNR5cp8Z